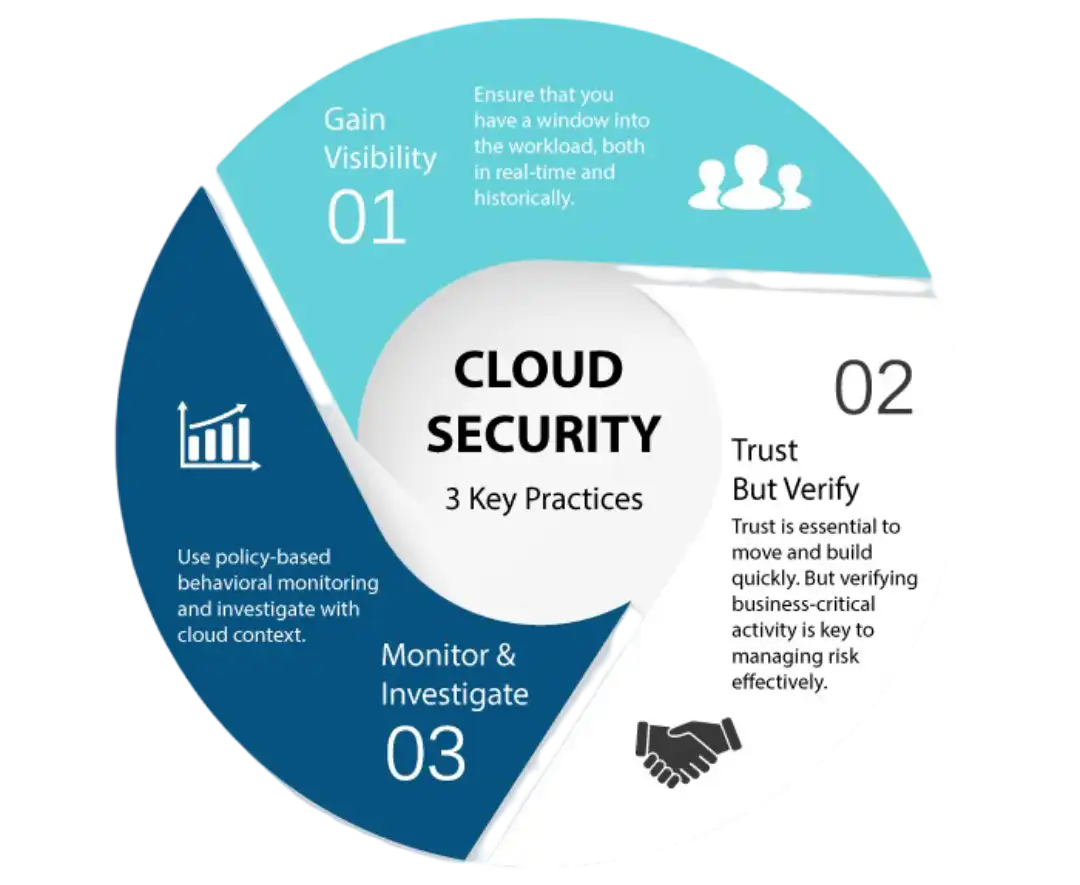
Cloud Infrastructure
Business Automation
Intelligence & Tools

Lead Ocean
NewWe built a large database of companies and use AI to match your business with perfect leads.

Business Intelligence as a Service
AI SupportTry PlusClouds Eaglet service and find high quality B2B hot leads and opportunities with AI support.
Need Leo on premise ?
Cost SaverEasily reduce your datacenter costs by 75% with Leo and its hardware solutions.

AutoQuill
MarketingAutoQuill writes and posts affiliate marketing content for you.
Industry
Solutions
Tailored technological frameworks for global enterprises.

Tourism Ecosystem
Global infrastructure for international market dominance.